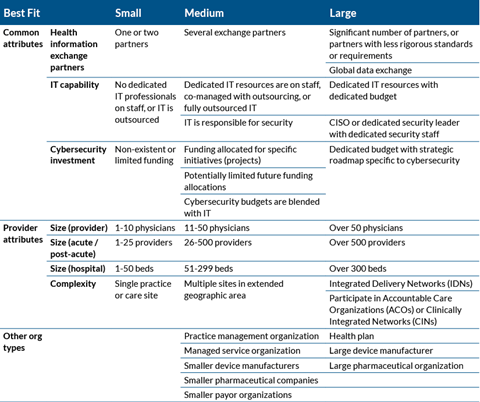
The Health Industry Cybersecurity Practices (“HICP”), also referred to as 405(d), is a set of guidelines and best practices that healthcare providers can leverage to enhance their cybersecurity program and better protect their patient data.
This set of guidelines was developed by U.S. Department of Health & Human Services (HHS) with the assistance of industry experts and provides an incredible resource for healthcare organizations to utilize within their IT security program. According to the HIPAA Security Rule, all covered entities are required by law to conduct an annual risk analysis. This would include areas such as specialists, ambulatory, family care, etc.
“The HIPAA Security Rule mandates that covered entities and business associates must complete an annual risk analysis to identify and document vulnerabilities and reasonably anticipated threats to the confidentiality, integrity, and availability of electronic protected health information (ePHI) that the organization creates, receives, maintains, or transmits.” – (45 CFR 164.308(a)(1)(ii)(A))
The completion of a risk assessment utilizing HICP meets this requirement. Let’s take a look at three reasons why HICP is a game changer for healthcare providers.