HITRUST Compliance

The HITRUST Common Security Framework (CSF) allows healthcare entities to demonstrate compliance with many different standards and regulations such as HIPAA, ISO, NIST, SOC 2, GDPR, PCI, CMS, MARS-E, and more. You can learn more about their background here: https://hitrustalliance.net/about-us/
One of a select group of HITRUST CSF assessors, LBMC Cybersecurity participated in the effort to integrate security standards from Centers for Medicare and Medicaid Services (CMS) and NIST into the HITRUST Alliance framework. In 2010, we became one of the first HITRUST CSF assessor organizations, making us exceptionally qualified to use HITRUST CSF to assure your organization’s information is safe and secure.
What is HITRUST?
HITRUST, in collaboration with leaders from the private sector, government, technology, and information privacy and security spaces, established the HITRUST CSF, a certifiable framework that can be used by any organization that creates, accesses, stores, or exchanges sensitive information.
Every organization can achieve the coveted HITRUST CSF Certification, but it will take a little patience, a lot of executive support, and, sometimes, a helping hand.
Learn more about HITRUST, HITRUST CSF, and the top six key benefits of using a HITRUST assessment.
On-Demand Webinar Duration: 0:05:47
Speaker:
- Robyn Barton, Shareholder, Practice Leader, HITRUST Authorized External Assessor Council & Quality Subcommittee Member

Do your policies and procedures address the HITRUST criteria?
Whether you are maintaining your existing HITRUST certification or pursuing certification for the first time, now may be a good time to review the HITRUST guidance and ensure your policies and procedures are up to par.
1. Policy and Procedure Applicability
The policy and procedure maturity levels and associated scoring are only applicable for a r2 assessment. Keep in mind, however, that even though focus of the e1 and i1 assessments is on control implementation only, some requirement statements will still necessitate review of policy and procedure documents.
2. Policy and Procedure Incubation Period
The minimum number of days that a remediated or newly implemented policy or procedure must be in place to be considered for scoring is 60 days. For organizations currently in the remediation phase, policy and procedure updates need to be in existence for 60 days in order to be assessed during testing. Additionally, for organizations undergoing a validated assessment, policies and procedures that have been in place for 60 days can be utilized. Note: the number of days for implemented, measured, and managed maturity levels is 90 days.
3. Policy and Procedure Scoring
Policy and procedure maturity levels are scored in accordance with the HITRUST Control Maturity Scoring Rubric based on a calculation of the strength of the policy or procedure, as well as the percentage of evaluative elements being addressed by the documentation.
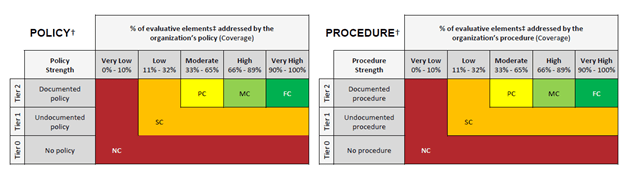
4. Policy and Procedure Format
HITRUST references the following definitions for policy and procedure.
| Document | Definition |
| Policy | Overall intention and direction as formally expressed by management, most often articulated in documents that record high-level principles or course of actions; the intended purpose is to influence and guide both present and future decision making to be in line with the philosophy, objectives and strategic plans established by the enterprise’s management teams. |
| Procedure | A detailed description of the steps necessary to perform specific operations in conformance with applicable standards. Procedures are defined as part of processes. |
Please note that HITRUST does not require that policy statements reside in only policy documents or that procedures reside in only procedure documents. Documentation can take many forms, including standards, handbooks, guidelines, directives, etc.
Misconceptions About HITRUST
HITRUST® continues to see tremendous growth and success in the marketplace by helping address the multitude of security, privacy and regulatory challenges facing organizations. As companies start their HITRUST journey we often hear common misconceptions.
1. Can you be certified to HIPAA?
Unfortunately, the HIPAA Security Rule’s numerous standards and implementation specifications for administrative, technical and physical safeguards, despite what the terms imply, lack the prescription necessary for actual implementation by a healthcare organization. The HITRUST CSF® is mapped to the HIPAA Security Rule, Breach Notification, and Privacy Rule as optional regulatory factors that can be selected for inclusion in a r2 assessment. When selected, these will provide reasonable assurance that your organization is satisfying the rule’s requirements. Additionally, HITRUST offers a MyCSF Compliance and Reporting Pack for HIPAA that compiles evidence from the r2 assessment and generates a report that parses applicable HIPAA requirements to an organization’s HITRUST assessment. This report can be shared directly with auditors or investigators to demonstrate compliance.
2. If I am not a healthcare entity, can I still be HITRUST certified?
Absolutely! HITRUST, in collaboration with privacy, information security and risk management leaders from the public and private sectors, develops, maintains and provides broad access to its widely-adopted risk and compliance management framework. It now includes 46+ mapped authoritative sources and has strong adoption rates across a broad spectrum of industries including manufacturing, banking, airline/entertainment, and telecommunications. Indeed, if you fall into any of these industries, you likely are hearing about HITRUST as a way to communicate your organization’s security and privacy practices using the HITRUST CSF.
3. A popular misconception is that HITRUST came about as a result of failed OCR HIPAA audits, is this true?
The OCR HIPAA audits did not begin until 2011. HITRUST was founded in 2007. LBMC has remained a steadfast supporter of the HITRUST CSF since February of 2010.
4. Can an organization certify to NIST CyberSecurity Framework?
The NIST Cybersecurity Framework (CSF) is a globally recognized set of standards that provides organizations the foundational elements necessary to design, assess, and mature their cybersecurity program.
HITRUST recognizes that many organizations prefer the reporting structure defined in the NIST Cybersecurity Framework. In conjunction with a r2 validated assessment, HITRUST issues a NIST CSF report scorecard that details an organization’s compliance with NIST Cybersecurity Framework-related controls included in the HITRUST CSF framework.
5. Is the HITRUST program a true Assess Once, Report Many™ audit program?
Yes. Experienced audit firms have developed processes to enable their staff to combine the criteria for multiple audit needs and apply those savings to your organization through increased efficiency, decreased audit fatigue, and higher quality, consistency and reliability of results. If an audit firm dissuades you from this approach, they may not have the staff skill or tools to execute properly.
6. Is the HITRUST CSF framework designed to allow me to become ISO 27001 certified?
The HITRUST CSF framework and certification process can be leveraged to assist with ISO 27001 certification efforts. As with any assessment, be sure to do your homework on your service provider’s skills and knowledge performing any assessment or readiness exam. There are many benefits that can be derived from combining security and/or privacy assessment testing when multiple reporting options are needed. When combining assessments, the intent and specific requirements of the certification must be taken into account – beginning at the planning stage of the project.
A great example of this is described in a recent HITRUST white paper. https://hitrustalliance.net/casestudy/leveraging-hitrust-mycsf-to-maintain-iso-27001-certification/ Here are a couple of points to consider from HITRUST’s FAQ on the subject, if you are seeking a firm that can support you in your pursuit of multiple certifications:
- The focus of an ISO 27001 certification is on the information security management system (ISMS), which includes an evaluation of the information security risk assessment and treatment processes. However, “organizations can design controls as required, or identify them from any source” (ISO 27001, § 6.1.3.b, p. 4). Further, although ISO 27001 Annex A contains a list of control objectives and controls, they are not exhaustive and additional control objectives and controls may be needed” (Ibid., § 6.1.3.c, p. 4). And although the ISO assessor must produce a “Statement of Applicability that contains the necessary controls (see 6.1.3 b and c) and justification for inclusions, whether they are implemented or not, and the justification for exclusions of controls from Annex A” (Ibid., § 6.1.3.d, p. 4), it doesn’t extend beyond what’s required in Annex A. Subsequently, organizations have wide latitude in the controls they specify to address the risks they identify at a level suitable to their risk appetite. ISO certification assessors also have some latitude in how they assess the effectiveness of the controls, and there is no quality control of the assessments other than a general requirement that consultants that help organizations prepare for ISO certification do not perform the certification assessment.
- The HITRUST CSF provides a baseline of comprehensive, prescriptive control requirements tailored to specific organizational, system and regulatory risk factors. Detailed testing procedures prescribed by these baseline requirements focuses on the maturity of this control baseline’s implementation using a specific, rigorous assessment approach and scoring model in order to gauge the level of excessive residual risk to ePHI in the organization. Like ISO, the testing must be performed by an approved assessor, referred to by HITRUST as an Authorized External Assessor Organization. Quality assurance is provided by HITRUST.
Client Testimonial
HITRUST Services
HITRUST Readiness and Expertise
As a HITRUST assessor, LBMC Cybersecurity’s experts can help ensure that your organization is prepared for HITRUST as you embark on the journey of certification and establishing a well-known and generally-accepted security framework within any industry.
HITRUST Certification
HITRUST has developed an assurance program that allows for independent HITRUST certification or validation against the framework. These validation or certification engagements must be performed by organizations (assessors) that have been specially trained and vetted by HITRUST as having experience and expertise specifically in healthcare information security.
HITRUST Interim Assessments
As required by HITRUST, an interim assessment must be completed as a follow-up after the first year of Certification. LBMC Cybersecurity can help provide this assessment to gauge the organization’s current state against the HITRUST CSF and will leverage any evidence gathered to submit an Annual Review Letter to HITRUST.
HITRUST Bridge Assessment
The COVID-19 pandemic has created difficulties in carrying out certain aspects of HITRUST CSF Assessments due to restrictions on travel, meetings, and access to company sites. In response, HITRUST issued guidance for requesting an extension to the certification period. If you are seeking an external assessor to perform the assessment, LBMC stands ready to assist you. With ten years of experience helping companies with their HITRUST needs, and the most experienced team in the industry, we aren’t going anywhere!
WEBINAR: HITRUST i1 Assessment
- What is the HITRUST i1 Implemented Verified Assessment and Certification?
- Why was this new option was created?
- Key differences between i1 vs r2.
- How to choose which option is right for you.
On-Demand Webinar Duration: 7:36
As the leader of the “10 year club” of assessors, LBMC stands as the longest-serving assessor in the business with the most experienced team in the industry. Back in February 2010, our leaders signed on the dotted line to join in a movement that has become the modern-day gold-standard in security and privacy assessments. We have cultivated a team of assessors led by experts who have been contributing to this success the longest.
We have helped countless organizations reach their HITRUST CSF Certification goal. And, yes, we have learned many lessons along the way. In fact, we are assessor council members and assist the industry with education and outreach. We feel compelled, and are somewhat obligated, to offer some words of encouragement and advice to those that are embarking on this journey. Please reach out any time with how we can assist you on your journey!
Executive Team
We’re happy to answer any questions you may have on what our security experts can do for you. Submit the form below and one of our professionals will get back to you promptly.
