According to recent research, a good number of internal auditors believe that the primary concern facing businesses is cybersecurity. These poll results emphasize the need of giving protecting of private corporate data far more attention.
Especially on cybersecurity, the 2024 North American Pulse of Internal Audit Benchmarks for Internal Audit Leaders by the Internal Audit Foundation provides vital information on the state of internal audit. The report contains key metrics and survey results conducted by the Foundation and includes data related to audit priorities and post-pandemic recovery.
This report has been a key source of guidance for internal audit and organizational leadership since 2008. It speaks to both current conditions and long-term trends in the internal audit space. By highlighting key areas of focus for internal audit functions, the report helps internal auditors prioritize their activities and allocate resources effectively to ensure that internal audit efforts are aligned with the most significant risks facing an organization.
The latest findings emphasize the prominent role of technology, especially cybersecurity and IT, as the primary areas of concern. Cybersecurity and IT have become the primary risks with more attention on third-party contacts, compliance/regulatory issues, and operational challenges.
Of the Chief Audit Executives and Directors surveyed, shockingly 78% believe the risk from cybersecurity issues is either extremely high or very low. That’s a significant increase from the 60% who felt that way in 2017. Only 21% of respondents say the risk is moderately high, and 1% believe the risk is low. This shows that auditors are more worried about cyber threats than ever before.
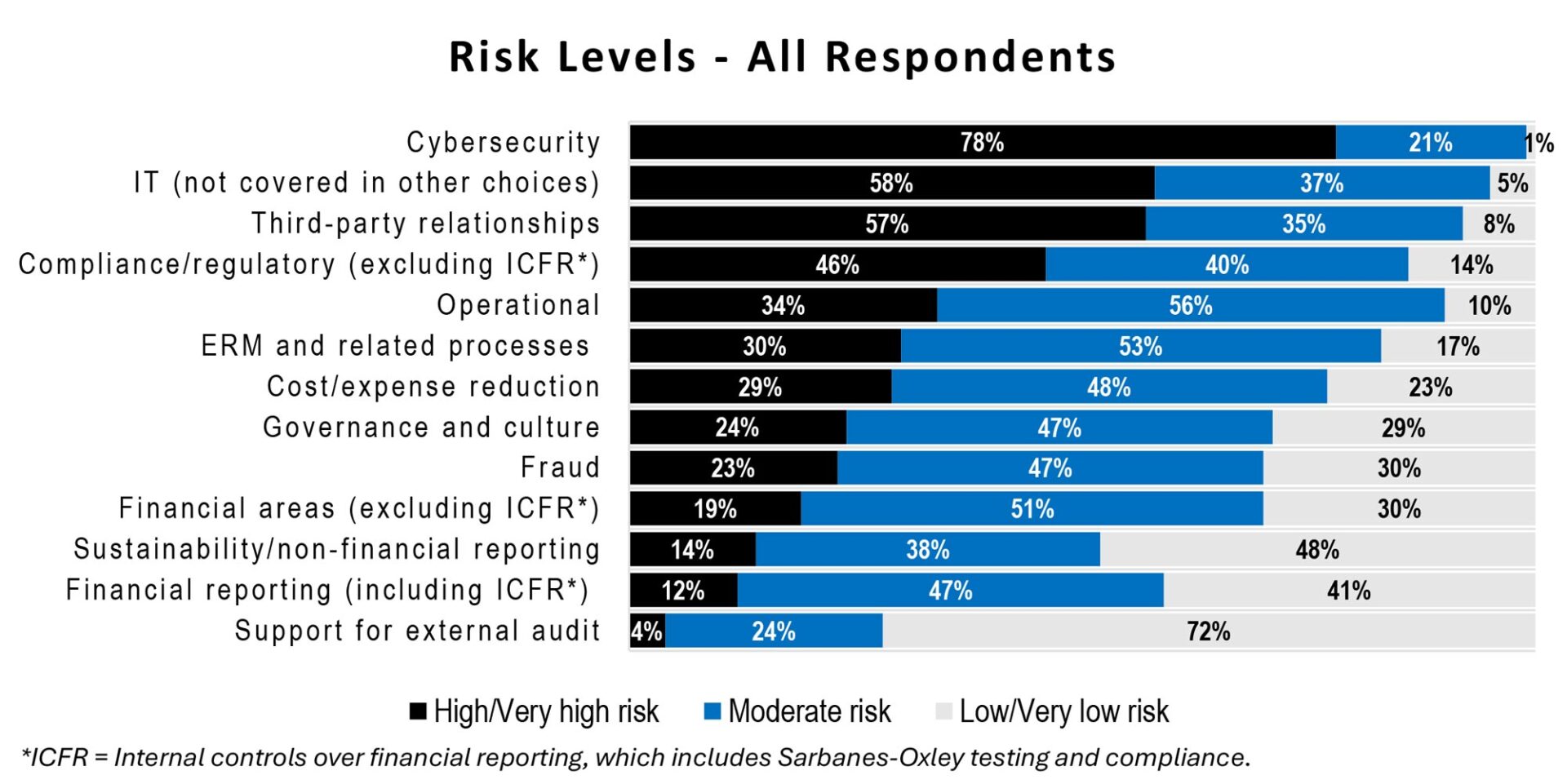
Overcoming the allocation for operational, financial reporting, and compliance/regulatory sectors, the survey shows that measures to handle cybersecurity and IT risks form about 20% of internal audit plans. This significant number highlights the increasing concern about cybersecurity and the need of a deliberate strategy to correctly manage these risks.

